This quick reference page provides a summary of the specifications of this topology. For a complete reference including installation details, please refer to the Security Router Pod Planning and Installation Guide
| Topology | Supports | Documentation |
|---|---|---|
|
FNSR 1.x | Planning and Installation Guide |
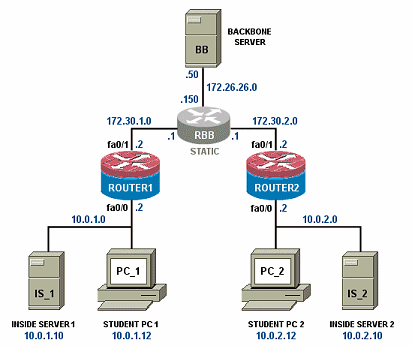
Lab devices are part of the topology and users can interact with them either directly through the console or network.
Hardware compatibility with NETLAB+ does not guarantee the compatibility of labs. Please check the Academy curriculum, NDG pod guides, and lab support pages for specific hardware and IOS requirements.
Other equipment may work if it is supported by NETLAB+ and can meet the minimum requirements for feature sets, interfaces, IOS, RAM, and Flash.
| Recommended Models |
Ethernet Ports Required |
IOS Release | Images (in order of preference) |
|---|---|---|---|
|
2611XM 2621XM 2651XM 26211 |
2 |
12.3(4)T Advanced IP Services 12.3(4)T Advanced Security |
C2600-advipservicesk9-mz.123.3-4.T6 (128/32) C2600-advsecurityk9-mz.12.3-4.T6 (96/32) |
VPN Router bundles ship by default with 12.3(4)T or later. Do not go above the 12.3(7)T image, as the IOS Intrusion Detection commands have changed significantly in version 12.3(8)T. If the router has 12.3(8)T or later, the image must be downgraded.
Security Device Manager (SDM) version 1.2 or later will be required for labs in Modules 2 through 7. VPN router bundles ship by default with SDM.
1The 2621 model router will work for all labs excluding SDM labs once they have been upgraded from 16F/32DRAM to 16F/64DRAM.
RBB is a static router. It is not accessible or configurable by users. However, it is part of the topology so users can indirectly interact with it (i.e. ping, trace, RIP, etc.).
You can implement RBB in one of two ways:
Configuration of each option is covered in detail in section 8 of the Planning and Installation Guide.
The Backbone Server (BB) provides services that are typically provided by Internet servers.
The FNS curriculum provides two options for the backbone server (BB):
NETLAB+ currently does not support the SuperServer (option 2). You should use VMware GSX (or other virtualization) products to simulate several machines. Virtual machines have their own routing tables, which avoids asymmetric routing problems in the pod.
FNSR refers to a Client-to-IOS Firewall configuration. NETLAB+ does not have a pod type for this topology. However, you may also configure the Backbone Server (BB) for direct access, which means that users can login and interact with the Windows interface.
By loading the Cisco VPN client software on BB, users can use the NETLAB+ Security Router Pod for client-to-IOS firewall labs. Direct access also allows BB to be used as an external PC for labs that require testing from an outside network (i.e. simulating the Internet).
The NETLAB+ interface name translation feature is supported on this pod type. This may influence the selection of modular interface cards and slot placement within the router. Please review the expected interface names for each router.
Remote PCs are implemented by integrating with 3rd party virtualization products. The NETLAB+ documentation library includes several guides with extensive detail on the implementation of virtualization with your NETLAB+ system.
The following operating system choices are typical based on the curriculum. These choices are not mandatory; you can make substitutions provided that:
The Security Router Pod includes placeholders for 5 remote PCs.
Control devices provide internal connectivity, console access, and managed power. Control devices are dynamically managed by NETLAB+ and are not accessible or configurable by end users.
| Control Device Resource | Quantity Required |
|---|---|
| Control Switch | 10 Consecutive Ports + up to 5 Reserved Ports |
| Access Server | 2 Lines |
| Switched Outlet Devices | 2 Outlets |
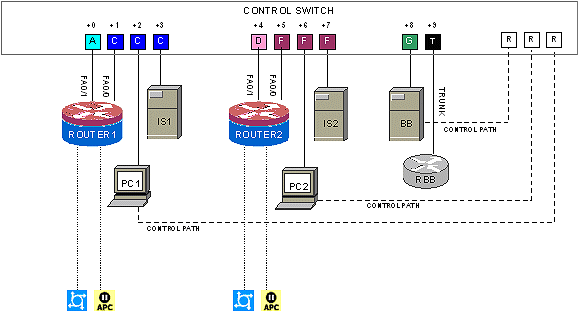
Please refer to the Security Router Pod Plan ning and Installation Guide