

This work by the National Information Security and Geospatial Technologies Consortium (NISGTC), and except where otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported License.
Development was funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48; The National Information Security, Geospatial Technologies Consortium (NISGTC) is an entity of Collin College of Texas, Bellevue College of Washington, Bunker Hill Community College of Massachusetts, Del Mar College of Texas, Moraine Valley Community College of Illinois, Rio Salado College of Arizona, and Salt Lake Community College of Utah.
This workforce solution was funded by a grant awarded by the U.S. Department of Labor's Employment and Training Administration. The solution was created by the grantee and does not necessarily reflect the official position of the U.S. Department of Labor. The Department of Labor makes no guarantees, warranties or assurances of any kind, express or implied, with respect to such information, including any information on linked sites, and including, but not limited to accuracy of the information or its completeness, timeliness, usefulness, adequacy, continued availability or ownership.
Ethical Hacking labs are supported in NETLAB+ using the Ethical Hacking (EH) Pod.
To enable the Ethical Hacking labs, check the box for "NISGTC Ethical Hacking" in the class settings. This must be done for each class requiring access to the labs.
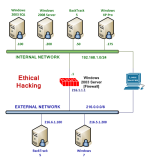
Always select the correct lab exercise for the lab being performed. Students or teams should schedule the correct lab exercise from the catalog. NETLAB+ will only show those labs for which the required pod type is available. A lab that works on different pod types may appear more than once if your system is so equipped. Instructors should select the correct lab from the Exercise tab during instructor-led lab reservations. This can be done as many times as needed during the reservation.
Importance of Choosing the Correct Lab Exercise
Several of the labs may differ from the standard pod topologies. This is
handled by NETLAB+ Dynamic VLAN Mapping technology. Always select the
correct lab exercise for the actual lab. This insures that NETLAB+
will set up VLANs on the control switch such that lab devices and PCs are
placed in the correct LAN segment for the exercise being performed. Selecting
the correct exercise will also make the completed lab output easier to find in
the archive.
| Lab | Title | Certified Ethical Hacking (CEH) Domain |
|---|---|---|
| 1 | Using Active and Passive Techniques to Enumerate Network Hosts |
|
| 2 | Conducting Active and Passive Reconnaissance Against a Target |
|
| 3 | Using the SYSTEM account |
|
| 4 | Poison Ivy – Remote Access Trojan |
|
| 5 | Using the SHARK Remote Administration Tool |
|
| 6 | Utilizing Malware - Dark Comet |
|
| 7 | Breaking Windows Passwords |
|
| 8 | Using John the Ripper to Crack Linux Passwords |
|
| 9 | Using Spear Phishing to Target an Organization |
|
| 10 | Breaking WEP and WPA Encryption |
|
| 11 | Using Metasploit to Attack a Remote System |
|
| 12 | Using Armitage to Attack the Network |
|
| 13 | Exploitation with IPv6 |
|
| 14 | Creating MSFPAYLOADS |
|
| 15 | Abusing SYSTEMS |
|
| 16 | SQL Injection |
|
| 17 | Launching a Buffer Overflow |
|
| 18 | Intrusion Detection |
|
| 19 | Using Certificates to Encrypt Email |
|