This quick reference page provides a summary of the specifications of the NDG Ethical Hacking v2 pod.
Two options for configuring the topology are shown below. Series-2 labs make use of a WinOS VM; a WinOS VM is not necessary to perform the Series-1 labs. The topology may be configured with or without a WinOS VM, depending on whether you plan to use the (Series-2) labs; see the install guide (linked below) for details.
| Topology | Supports... | Documentation |
|---|---|---|
NDG-EH v2 Pod
|
You may request virtual machine templates for the NDG Ethical Hacking v2 pod from CSSIA.
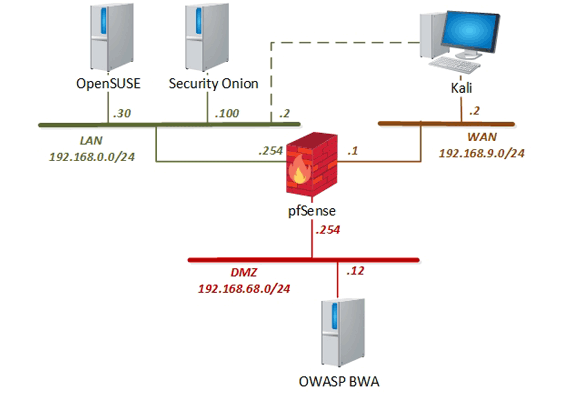
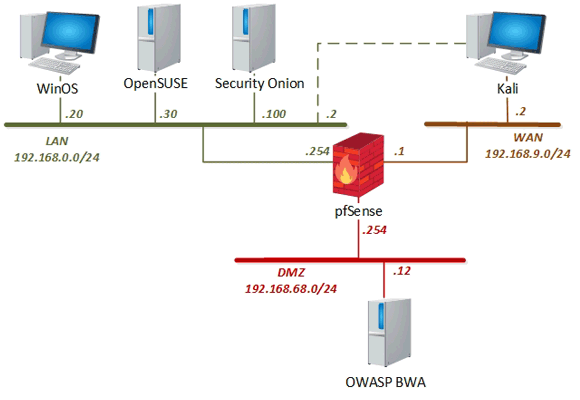
The following table provides details of the storage requirements for each of the virtual machines in the pod.
The Ethical Hacking v2 course will consume 83.9 GB of storage per each master pod instance. If you choose to only teach Series-1 labs, then the course will consume 53.7 GB of storage per each master pod instance due to the removal of the WinOS virtual machine.
| Virtual Machine | OVF/OVA | Initial Master Pod (Thin Provisioned) |
Maximum Allocated Memory |
|---|---|---|---|
| Kali | 7.1 GB | 17.9 GB | 2 GB |
| OpenSUSE | 3.9 GB | 8.6 GB | 2 GB |
| OWASP-BWA | 2.8 GB | 6.9 GB | 1 GB |
| pfSense | 717.9 MB | 1.3 GB | 512 MB |
| Security Onion | 5.7 GB | 19 GB | 2 GB |
| WinOS | 16.3 GB | 30.2 GB | 8 GB |
| Total | 36.52 GB | 83.9 GB | 15.5 GB |
The virtual machines are made available as Open Virtualization Format (OVF) or Open Virtualization Archive (OVA) files. These files are available for download from EPNC (Education Pathway National Center).
To request access to the preconfigured virtual machine templates from EPNC: