NDG Ethical Hacking v2, developed by NDG, focuses on one of the most challenging sectors of cybersecurity. This series of labs is designed to provide hands-on experience conducting a variety of ethical hacking practices. These skills can help prepare trainees for a variety of IT positions, including: Cybersecurity Analyst, Penetration Tester, Ethical Hacker-Security Engineer, IT Security Specialist, Cybersecurity Engineer, and Information Security Engineer.
The labs map to several leading industry certifications, as noted in the Supported Labs tables below.
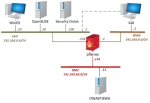
NDG Ethical Hacking v2 (Series-1 and Series-2) labs are supported in NETLAB+ using the NDG Ethical Hacking v2 Pod. Series-2 labs make use of a WinOS VM; a WinOS VM is not necessary to perform the Series-1 labs. The topology may be configured with or without a WinOS VM, depending on whether you plan to use the Series-2 labs. See the NDG Ethical Hacking v2 Pod page for details.
Material in these labs aligns to the books/certifications shown in the table below.
| Lab | Title | All-In-One CEH Chapters ISBN-13: 978-1260454550 |
EC-Council CEH v10 Domain Modules | CompTia Pentest+ Objectives | CompTIA All-In-One PenTest+ Chapters ISBN-13: 978-1260135947 |
|---|---|---|---|---|---|
| 1 | DNS Footprinting |
|
|
|
|
| 2 | Packet Crafting with Scapy |
|
|
|
|
| 3 | Reconnaissance with Nmap, Zenmap, and Masscan |
|
|
|
|
| 4 | Reconnaissance with HPing |
|
|
|
|
| 5 | Vulnerability Scanning with OpenVAS |
|
|
|
|
| 6 | Network Analysis |
|
|
|
|
| 7 | Evading IDS |
|
|
|
|
| 8 | Password Cracking with John the Ripper and Hashcat |
|
|
|
|
| 9 | Metasploit Framework Fundamentals and Armitage |
|
|
|
|
| 10 | Web Pentesting |
|
|
|
|
| 11 | Client Side Exploitations |
|
|
|
|
| 12 | ARP Spoofing and MiTM Attacks |
|
|
|
|
| 13 | Understanding Buffer Overflows |
|
|
|
|
| 14 | Understanding SQL Commands & Injections |
|
|
|
|
| 15 | Backdooring with Netcat |
|
|
|
|
| 16 | VNC as a Backdoor |
|
|
|
|
| 17 | Creating and Installing SSL Certificates |
|
|
|
|
| 18 | Social Engineering Attacks with Social Engineering Toolkit |
|
|
|
|
Material in these labs aligns to the books/certifications shown in the table below.
| Lab | Title | All-In-One CEH Chapters ISBN-13: 978-1260454550 |
EC-Council CEH v10 Domain Modules |
|---|---|---|---|
| 19 | Scanning Methodology |
|
|
| 20 | Enumeration |
|
|
| 21 | System Hacking |
|
|
| 22 | Registry – Windows Security Account Manager |
|
|
| 23 | Covering Your Tracks |
|
|
| 24 | Web-Based Hacking |
|
|
| 25 | Mobile Hacking |
|
|
| 26 | Cryptography |
|
|
The books listed below are recommended resources to accompany the NDG Ethical Hacking v2 labs.
CEH Certified Ethical Hacker All-in-One Exam Guide 4th Edition by Matt Walker ISBN-13: 978-1260454550 ISBN-10: 126045455X CompTIA PenTest+ Certification All-in-One Exam Guide (Exam PT0-001) 1st Edition by Raymond Nutting ISBN-13: 978-1260135947 ISBN-10: 1260135942
To enable the NDG Ethical Hacking v2 labs, install the NDG Ethical Hacking - v2 course using the Course Manager. See the Course Manager section of the NETLAB+ VE Admin Guide for details. The course content will then be available to be added to classes.
Always select the correct lab exercise for the lab being performed. Students or teams should schedule the correct lab exercise from the catalog. NETLAB+ will only show those labs for which the required pod type is available. A lab that works on different pod types may appear more than once if your system is so equipped. Instructors should select the correct lab from the Exercise tab during instructor-led lab reservations. This can be done as many times as needed during the reservation.