NDG has worked closely with the EMC Academic Alliance to develop these labs and to ensure compatibility with NETLAB+.
The NETLAB+ EMC ISM pod is used to support the EMC Information Storage and Management (ISM) course. All lab components are 100% virtualized to achieve a high pod to physical host ratio, at a significantly lower cost point relative to traditional delivery of ISM. Using virtualization and the sharing and scheduling capabilities of NETLAB+, each student (or team of students) has access to their own set of virtual equipment, which they may maintain exclusive use of throughout the course.
Please review the content-specific requirements for ISM labs.
NETLAB+ is the ideal hands-on supplement to use with Information Storage and Management: Storing, Managing, and Protecting Digital Information in Classic, Virtualized, and Cloud Environments, 2nd Edition, to teach the ISM course.
To enable the EMC ISM labs, check the box for "EMC ISM Labs" in the class settings. This must be done for each class requiring access to the labs.
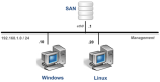
Always select the correct lab exercise for the lab being performed. Students or teams should schedule the correct lab exercise from the catalog. NETLAB+ will only show those labs for which the required pod type is available. A lab that works on different pod types may appear more than once if your system is so equipped. Instructors should select the correct lab from the Exercise tab during instructor-led lab reservations. This can be done as many times as needed during the reservation.
Importance of Choosing the Correct Lab Exercise
Several of the labs may differ from the standard pod topologies. This is
handled by NETLAB+ Dynamic VLAN Mapping technology. Always select the
correct lab exercise for the actual lab. This insures that NETLAB+
will set up VLANs on the control switch such that lab devices and PCs are
placed in the correct LAN segment for the exercise being performed. Selecting
the correct exercise will also make the completed lab output easier to find in
the archive.
| Lab | Description |
|---|---|
| 1 | Introduction to Storage |
| 2 | Overview of RAID |
| 3 | Overview of LUNs |
| 4a | Overview of Network-Attached Storage |
| 4b | Analyze Protocols and Performance of Network-Attached Storage |
| 5 | Overview of iSCSI |
| 6 | Backup and Recovery |
| 7a | Identifying Security Vulnerabilities |
| 7b | Securing the Storage Infrastructure |
| 8 | Managing the Storage Infrastructure |