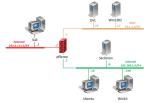
Security+ is a vendor-neutral certification that proves competency in network security and risk management. Security+ labs focus on the principles and best practices in network security. Students gain hands-on practice in the skills needed to secure a network and prepare for industry certification.
Security+ labs are supported in NETLAB+ using the Security+ v3 Pod.
| Lab | Title | Mappings to Exam Objectives |
|---|---|---|
| 01 | Investigating ARP Poisoning | 1.2: Compare and contrast type of attacks |
| 02 | Password Cracking with Linux | 1.2: Compare and contrast type of attacks |
| 03 | Password Cracking with Windows | 2.2: Given a scenario use appropriate software tools to assess the security posture of an organization 1.2: Compare and contrast type of attacks |
| 04 | Performing Active Reconnaissance with Windows | 1.4: Explain penetration testing concepts |
| 05 | Performing Active Reconnaissance with Linux | 2.2: Given a scenario, use appropriate software tools to assess the security posture of an organization 1.5: Explain Vulnerability scanning concepts |
| 06 | Wireless Networking Attack and Mitigation Techniques | 1.2: Compare and contrast type of attacks |
| 07 | Analyze and Differentiate Types of Attacks and Mitigations Techniques | 1.2: Compare and contrast type of attacks |
| 08 | Analyze and Differentiate Types of Malware and Application Attacks | 1.1: Given a scenario, analyze indicators of compromise and determine the types of malware |
| 09 | Analyzing Types of Web Application Attacks | 1.2: Compare and contrast type of attacks |
| 10 | Basic Command Line Tool Techniques | 2.2: Given a scenario use appropriate software tools to assess the security posture of an organization |
| 11 | Configuring a Network-Based Firewall | 2.1: Install and configure network components, both hardware and software-based, to support organizational security 3.2: Given a scenario, implement secure network architecture |
| 12 | Identifying & Analyzing Network/Host Intrusion Detection System Alerts | 2.3: Given a scenario, troubleshoot common security issues |
| 13 | Secure Network Administration Principles Log Analysis | 2.3: Given a scenario, troubleshoot common security issues |
| 14 | Implementing Common Protocols and Services for Basic Security Practices | 2.1: Install and configure network components, both hardware and software-based, to support organizational security 2.6: Given a scenario implement secure protocols |
| 15 | Working with Android | 2.5: Given a scenario deploy devices securely |
| 16 | Connecting to a Remote System | 2.2: Given a scenario, use appropriate software tools to assess the security posture of an organization 2.6: Given a scenario, implement secure protocols |
| 17 | Capturing Network Traffic | 2.2: Given a scenario, use appropriate software tools to assess the security posture of an organization |
| 18 | Incident Response Procedures | 1.2: Compare and contrast types of attacks 5.4: Given a scenario, follow incident response procedures |
| 19 | Cryptography Concepts | 2.2: Given a scenario use appropriate software tools to assess the security posture of an organization |
| 20 | Configuring a RADIUS Server with Windows | 2.1: Install and configure network components, both hardware and software, to support organizational security |
| 21 | Windows Server Group Policy Object | 4.4: Given a scenario, differentiate common account management practices |
| 22 | Linux Account Management | 4.4: Given a scenario, differentiate common account management practices |
| 23 | PKI Management with Windows | 6.4: Given a scenario implement public key infrastructure |
| 24 | Performing Backups | 5.6: Explain disaster recovery and continuity of operations concepts |
| 25 | Securing Data with Encryption Software | 6.1: Compare and contrast basic concepts of cryptography |
NETLAB+ VE: To enable the Security+ v3 labs, install the NDG Security+ v3 course using the Course Manager. See the Course Manager section of the NETLAB+ VE Admin Guide for details. The course content will then be available to be added to classes.
NETLAB AE/PE: To enable the Security+ v3 labs, create a class and check the box for NDG Security+ v3 in the global labs class settings.