This is the 2nd version of the CSSIA CompTIA Security+® Lab Series. We recommend that you use the latest version, NDG Security+ v3, when starting a new class.

The original development of this lab series was funded by the National Science Foundation’s (NSF) Advanced Technological Education (ATE) program Department of Undergraduate Education (DUE) Award No. 0702872 and 1002746; Center for Systems Security and Information Assurance (CSSIA) at Moraine Valley Community College (MVCC).
This lab series has been adapted by The Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. The National Information Security, Geospatial Technologies Consortium (NISGTC) is authorized to create derivatives of identified elements modified from the original works. These elements are licensed under the Creative Commons Attributions 3.0 Unported License. To view a copy of this license, visit http://creativecommons.org/licenses/by/3.0/ or send a letter to Creative Commons, 444 Castro Street, Suite 900, Mountain View, California, 94041, USA. The Network Development Group (NDG) is given a perpetual worldwide waiver to distribute per US Law this lab and future derivatives of these works.
The adaption includes the addition of four new labs (7, 8, 18 and 20), as indicated in the list of supported labs below.
The Center for Systems Security and Information Assurance (CSSIA) in partnership with the Network Development Group (NDG) is given a perpetual worldwide waiver to distribute per US Law these labs and future derivatives of these works.
CSSIA CompTIA Security+® Labs - v2 are supported in NETLAB+ using the Multi-purpose Security (MSEC) Pod.
To enable the CSSIA CompTIA Security+® labs - v2, check the box for "CompTIA Security+® Labs - v2" in the class settings. This must be done for each class requiring access to the labs.
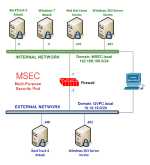
Always select the correct lab exercise for the lab being performed. Students or teams should schedule the correct lab exercise from the catalog. NETLAB+ will only show those labs for which the required pod type is available. A lab that works on different pod types may appear more than once if your system is so equipped. Instructors should select the correct lab from the Exercise tab during instructor-led lab reservations. This can be done as many times as needed during the reservation.
Importance of Choosing the Correct Lab Exercise
Several of the labs may differ from the standard pod topologies. This is
handled by NETLAB+ Dynamic VLAN Mapping technology. Always select the
correct lab exercise for the actual lab. This insures that NETLAB+
will set up VLANs on the control switch such that lab devices and PCs are
placed in the correct LAN segment for the exercise being performed. Selecting
the correct exercise will also make the completed lab output easier to find in
the archive.
| Lab | Title | CSSIA CompTIA Security+®Domain | Tasks Included |
|---|---|---|---|
| 1 | Network Devices and Technologies - Capturing Network Traffic | Network Security |
|
| 2 | Secure Network Administration Principles - Log Analysis | Network Security |
|
| 3 | Protocols and Default Network Ports - Transferring Data Using TCP/IP | Network Security |
|
| 4 | Protocols and Default Network Ports - Connecting to a Remote System | Network Security |
|
| 5 | Secure Implementation of Wireless Networking | Network Security |
|
| 6 | Incident Response Procedures | Compliance and Operational Security |
|
| 7 | Configuring the pfSense Firewall - NEW | Network Security |
|
| 8 | Configuring Backups - NEW | Compliance and Operational Security |
|
| 9 | Analyze and Differentiate Types of Malware | Threats and Vulnerabilities |
|
| 10 | Analyze and Differentiate Types of Attacks Using Window Commands | Threats and Vulnerabilities |
|
| 11 | Analyze and Differentiate Types of Application Attacks | Threats and Vulnerabilities |
|
| 12 | Mitigation and Deterrent Techniques - Anti Forensic | Threats and Vulnerabilities |
|
| 13 | Mitigation and Deterrent Techniques - Password Cracking | Threats and Vulnerabilities |
|
| 14 | Discovering Security Threats and Vulnerabilities | Threats and Vulnerabilities |
|
| 15 | Importance of Data Security - Data Theft | Application, Data and Host Security |
|
| 16 | Importance of Data Security - Securing Data Using Encryption Software | Application, Data and Host Security |
|
| 17 | Authentication, Authorization and Access Control | Access Control and Identity Management |
|
| 18 | Access Controls - NEW | Access Control and Identity Management |
|
| 19 | General Cryptography Concepts | Cryptography |
|
| 20 | Cryptography - NEW | Cryptography |
|
Jesse Varsalone has 21 years of teaching experience and has taught computer classes for The Community College of Baltimore County, Champlain College, Johns Hopkins University, Stevenson University, Towson University, University of Maryland Baltimore County and University of Maryland University College. Jesse has taught courses in Computer Security, Hacking, Intrusions, Forensics and Network Administration. Jesse Varsalone holds the CISSP, MCT, CTT+, CEH, Security+ and other certifications. His latest book, Defense against the Black Arts: How Hackers Do What They Do and How to Protect against It, is available at http://tinyurl.com/jessebook.