This quick reference page provides a summary of the specifications of the Network Security pod.


This work by the National Information Security and Geospatial Technologies Consortium (NISGTC), and except where otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported License.
Development was funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48; The National Information Security, Geospatial Technologies Consortium (NISGTC) is an entity of Collin College of Texas, Bellevue College of Washington, Bunker Hill Community College of Massachusetts, Del Mar College of Texas, Moraine Valley Community College of Illinois, Rio Salado College of Arizona, and Salt Lake Community College of Utah.
This workforce solution was funded by a grant awarded by the U.S. Department of Labor's Employment and Training Administration. The solution was created by the grantee and does not necessarily reflect the official position of the U.S. Department of Labor. The Department of Labor makes no guarantees, warranties or assurances of any kind, express or implied, with respect to such information, including any information on linked sites, and including, but not limited to accuracy of the information or its completeness, timeliness, usefulness, adequacy, continued availability or ownership.
| Topology | Supports... | Documentation |
|---|---|---|
Network Security Pod
|
You may request virtual machine templates for the Network Security pod from CSSIA.
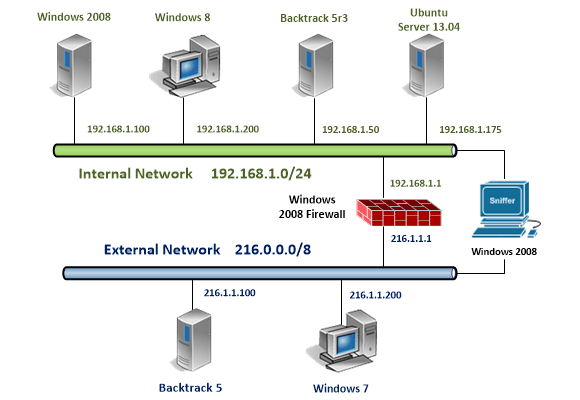
The virtual machines in the Network Security Pod are listed in the table below.
| Virtual Machine Topology Name | Virtual Machine Deployment Name |
|---|---|
| Windows 2008 | Net_Security_Master_Win2008 |
| Windows 8 | Net_Security_Master_Win8 |
| Backtrack 5R3 Internal | Net_Security_Master_BT5Int |
| Ubuntu | Net_Security_Master_Ubuntu |
| Windows 2008 Firewall | Net_Security_Master_Win2008Fw |
| Windows 2008 Sniffer | Net_Security_Master_Win2008Sniff |
| Backtrack 5 External | Net_Security_Master_BT5Ext |
| Windows 7 | Net_Security_Master_Win7 |
The virtual machines are made available as Open Virtualization Format (OVF) or Open Virtualization Archive (OVA) files. These files are available for download from EPNC (Education Pathway National Center).
To request access to the preconfigured virtual machine templates from EPNC: